Stay up to date the most pressing cyber threats, emerging trends and what they mean for enterprise security, critical infrastructure and global risk.
TLP: CLEAR
The week of July 26 - August 1, 2025 witnessed the most severe coordinated zero-day exploitation campaign of the year, with Chinese nation-state actors compromising over 75 organizations globally through Microsoft SharePoint vulnerabilities. This campaign coincided with a cascade of critical infrastructure attacks spanning telecommunications, aviation, government services, and financial sectors, indicating an escalation in both nation state and criminal threat actor capabilities. Russian threat actor Secret Blizzard conducted sophisticated ISP-level espionage operations against foreign embassies in Moscow, while ransomware operations reached critical thresholds with imminent data release deadlines affecting global supply chains.
The period marked multiple unprecedented incidents including the first state-level cyber emergency declaration in Minnesota requiring National Guard activation, massive telecommunications disruptions affecting 291 million Orange Telecom customers across 26 countries, and the destruction of 7,000 servers in coordinated attacks against Russian aviation infrastructure. Intelligence indicates threat actors are exploiting enterprise infrastructure vulnerabilities with unprecedented speed and coordination, requiring immediate defensive posture adjustments across critical sectors.
Analyst Comment: The convergence of nation-state zero-day capabilities with criminal ransomware operations- and the targeting of critical - targeting represents a fundamental shift in the threat landscape, requiring organizations to assume compromise within hours rather than traditional monthly vulnerability management cycles.
CRITICAL INCIDENTS
1. Chinese APTs Execute Mass SharePoint Zero-Day Campaign
Microsoft confirmed active exploitation of SharePoint Server zero-day vulnerabilities CVE 2025-53770 (CVSS 9.8) and CVE-2025-53771 beginning July 7, 2025, with Chinese nation state actors Linen Typhoon (APT27), Violet Typhoon, and Storm-2603 compromising over 75 organizations globally.1 The "ToolShell" attack campaign targets on-premises SharePoint servers to deploy persistent web shells named "spinstall0.aspx," extracting cryptographic keys and maintaining persistent access while bypassing multi-factor authentication and single sign-on controls.2 Check Point Research documented over 4,600 compromise attempts against more than 300 organizations worldwide, with confirmed breaches affecting government agencies including the US Energy Department's National Nuclear Security Administration.3
Analyst Comment: This represents the largest coordinated zero-day exploitation campaign of 2025, requiring immediate disconnection of internet-facing SharePoint servers and assumption of compromise for any exposed systems during the exploitation window.
2. Orange Telecom France Hit by Major Cyberattack
Orange detected a cyberattack on July 25, 2025, affecting information systems and causing service disruptions primarily in France, impacting the telecommunications provider's 291 million customers globally across 26-country operations.4 Orange Cyberdefense division isolated affected systems to limit impact, with full restoration expected by July 30.5 The attack represents one of the largest telecommunications infrastructure compromises in Europe during 2025, though no evidence of data exfiltration has been confirmed at this time.6 The French telecommunications sector has experienced increased targeting by state sponsored groups, particularly China-linked actors, according to ANSSI recommendations.
Analyst Comment: Major telecommunications infrastructure attacks create cascading effects across dependent services and highlight the vulnerability of critical communications infrastructure to sophisticated threat actors.
3. SafePay Sets August 1 Deadline for Ingram Micro Data Release
SafePay ransomware group established an August 1, 2025 deadline for releasing 3.5TB of data allegedly stolen from global technology distributor Ingram Micro following a July 3 ransomware attack that disrupted the AI-powered Xvantage distribution platform and Impulse license provisioning services.7 The attack initially compromised Ingram Micro's GlobalProtect VPN using compromised credentials, consistent with SafePay's established attack patterns as the most active ransomware group in May 2025 with 58 victims.8Ingram Micro's 57-country operations serving over 300,000 customers including Apple, HP, and Cisco face potential downstream supply chain impacts from data exposure.
Analyst Comment: The imminent data release creates immediate supply chain risk for organizations dependent on Ingram Micro's distribution services, requiring enhanced monitoring for credential compromise and business continuity planning.
4. Russian Aeroflot Cyberattack Forces 100+ Flight Cancellations
Pro-Ukrainian hacker groups Silent Crow and Belarus Cyber Partisans executed a devastating cyberattack against Russian airline Aeroflot on July 28, 2025, forcing the cancellation of over 100 flights and causing widespread operational disruption.9 The attack, described as one of the most disruptive cyberattacks against Russia since its invasion of Ukraine, reportedly destroyed 7,000 servers and compromised 20 terabytes of data.10 Silent Crow claimed they had infiltrated Aeroflot's networks for nearly a year before executing the attack.11 Russian prosecutors confirmed the incident as a "hacker attack" and opened a criminal investigation, with the attack affecting domestic and international routes to Belarus, Armenia, and Uzbekistan.
Analyst Comment: This incident demonstrates the operational disruption capabilities of hacktivist groups and highlights the vulnerability of aviation infrastructure to prolonged network infiltration and data destruction attacks.
ACTIVE THREAT ACTORS
Scattered Spider (UNC3944/0ktapus)
Scattered Spider escalated operations against VMware ESXi hypervisors using social engineering attacks against IT help desks to gain Active Directory access, then pivoting to vSphere environments to execute "disk-swap" attacks and deploy ransomware directly from hypervisor level.12 Google Threat Intelligence documented the group's capability to complete full attack chains within hours, targeting retail, airline, transportation, and insurance sectors across North America. The group recently incorporated DragonForce ransomware variant into operations while maintaining consistent tactics including phishing, push bombing, and SIM swap attacks to bypass multi-factor authentication.13 CISA and Five Eyes partners released an updated joint advisory July 29 emphasizing the group's expansion into commercial facilities sectors with data extortion capabilities targeting critical infrastructure organizations.
Chinese APT Coordination: Linen Typhoon, Violet Typhoon, Storm-2603
Microsoft attributed the coordinated SharePoint exploitation campaign to three distinct Chinese nation-state actors demonstrating unprecedented coordination in zero-day weaponization. Linen Typhoon (APT27) leads the campaign with advanced persistent access capabilities, while Violet Typhoon provides complementary infrastructure targeting and Storm-2603 conducts specialized exploitation techniques.14 The campaign demonstrates sophisticated understanding of SharePoint's internal architecture and cryptographic systems, with threat actors deploying custom web shells capable of extracting authentication keys and maintaining persistence across system reboots. Attribution confidence remains high based on infrastructure overlaps, timing analysis, and tactical signatures consistent with previous Chinese APT operations targeting government, telecommunications, and software sectors in North America and Western Europe.
Russian Secret Blizzard (FSB-affiliated)
Secret Blizzard has been conducting adversary-in-the-middle attacks targeting foreign embassies in Moscow, deploying ApolloShadow malware disguised as Kaspersky antivirus updates.15 The campaign leverages Russia's SORM surveillance systems to maintain persistent access to diplomatic communications, representing a significant escalation in nation-state espionage capabilities. Operations ongoing since at least 2024 demonstrate the group's ability to manipulate legitimate security software distribution channels within Russian telecommunications infrastructure. The campaign targets diplomatic personnel through compromised local ISPs and telecom services, requiring diplomatic missions to implement encrypted tunnels and avoid Russian-hosted infrastructure for sensitive communications.
GOOD NEWS
Cambodia Dismantles Major Cybercrime Operations
Cambodian Prime Minister Hun Manet ordered a nationwide crackdown on cybercrime operations, resulting in over 1,000 arrests across five provinces during the week of July 15, 2025.16 The arrests included 85 Cambodians and hundreds of foreign nationals from Vietnam, China, Taiwan, Indonesia, Myanmar, and Bangladesh operating in cybercrime compounds. The crackdown targets what the UN estimates as a multi-billion dollar scam industry operating from Southeast Asia, with operations involving romance and investment scams, human trafficking, and forced labor in cybercrime facilities.17
US Disrupts North Korean IT Revenue Scheme
The Department of Justice sentenced Christina Chapman to 102 months in prison for operating a "laptop farm" that enabled North Korean IT workers to fraudulently obtain remote jobs at 309 US companies using 68 stolen American identities, generating $17.1 million in revenue for the North Korean government.18 Treasury Department imposed sanctions on Korea Sobaeksu Trading Company and three individuals for sanctions evasion activities. The coordinated law enforcement operation included searches of 29 suspected laptop farms across 16 states, demonstrating successful disruption of state-sponsored revenue generation schemes.
Proactive Threat Hunting Prevents Infrastructure Compromise
CISA and US Coast Guard completed a joint proactive threat hunt at a US critical infrastructure organization that successfully identified significant cybersecurity risks before malicious exploitation occurred.19 While no malicious activity was detected, the hunt revealed critical vulnerabilities including plaintext credential storage, insufficient IT/OT network segmentation, and inadequate logging capabilities. The organization received comprehensive mitigation guidance and the findings were shared broadly to improve cybersecurity across the critical infrastructure community, demonstrating the value of proactive defensive operations.
Rapid International Coordination Counters Threat Actor Evolution
CISA and Five Eyes partners (FBI, Canadian Centre for Cyber Security, RCMP, Australian agencies) released a coordinated advisory on Scattered Spider threat group within days of identifying new DragonForce ransomware capabilities and expanded targeting patterns.20 The rapid international intelligence sharing and joint advisory publication demonstrates improved threat response coordination and provides actionable intelligence for defending against social engineering attacks targeting commercial facilities and critical infrastructure sectors.
TRENDS
Zero-Day Weaponization Acceleration
The first half of 2025 witnessed extreme vulnerability exploitation volatility with 432 CVEs showing evidence of exploitation in the wild, representing a 246% increase in vulnerability disclosures and 179% increase in publicly-available exploits compared to 2024.21 Analysis indicates 32.1% of vulnerabilities are being exploited on or before the day of CVE disclosure, demonstrating unprecedented speed in weaponization capabilities. Information-stealing malware credential theft skyrocketed by 800%, while ransomware incidents rose 179% and data breaches surged 235% in first half 2025.22 The National Vulnerability Database maintains a backlog of nearly 42,000 vulnerabilities awaiting analysis, creating critical intelligence gaps for defensive operations.
Analyst Comment: The acceleration in exploit development and deployment requires fundamental shifts in patch management strategies, with organizations needing to assume compromise within hours of vulnerability disclosure rather than traditional monthly patch cycles.
Critical Infrastructure Targeting Sophistication
State and local government entities experienced unprecedented targeting sophistication, with attacks escalating beyond traditional data theft to operational disruption requiring emergency response activation. The St. Paul (MN) emergency declaration represents broader trend of threat actors targeting municipal infrastructure to create public pressure and demonstrate capability against critical services.23 CISA's joint threat hunt with US Coast Guard revealed systemic cybersecurity deficiencies across critical infrastructure organizations, including plaintext credential storage, insufficient network segmentation, and inadequate logging capabilities.24 Multiple critical infrastructure sectors experienced major incidents during the collection period, including telecommunications (Orange), aviation (Aeroflot), government services (St. Paul), and financial services (Allianz Life), indicating coordinated or opportunistic targeting across essential services.
Social Engineering Campaign Evolution
Intelligence indicates sophisticated evolution in social engineering tactics, with threat actors successfully compromising major organizations through third-party systems and help desk manipulation. Allianz Life confirmed a data breach affecting the "majority" of its 1.4 million customers after threat actors gained access to a third-party cloud-based CRM system using social engineering techniques.25 The incident follows a pattern attributed to Scattered Spider threat group targeting the insurance sector, utilizing deceptive helpdesk calls to gain network access. North Korean IT workers generated $17.1 million in revenue through fraudulent remote employment at 309 US companies using 68 stolen American identities, with one Arizona woman operating a "laptop farm" receiving 102 months imprisonment.26 These incidents demonstrate the increasing sophistication and financial motivation behind social engineering campaigns targeting both direct access and supply chain vulnerabilities.
VULNERABILITIES
Critical Patches Required This Week
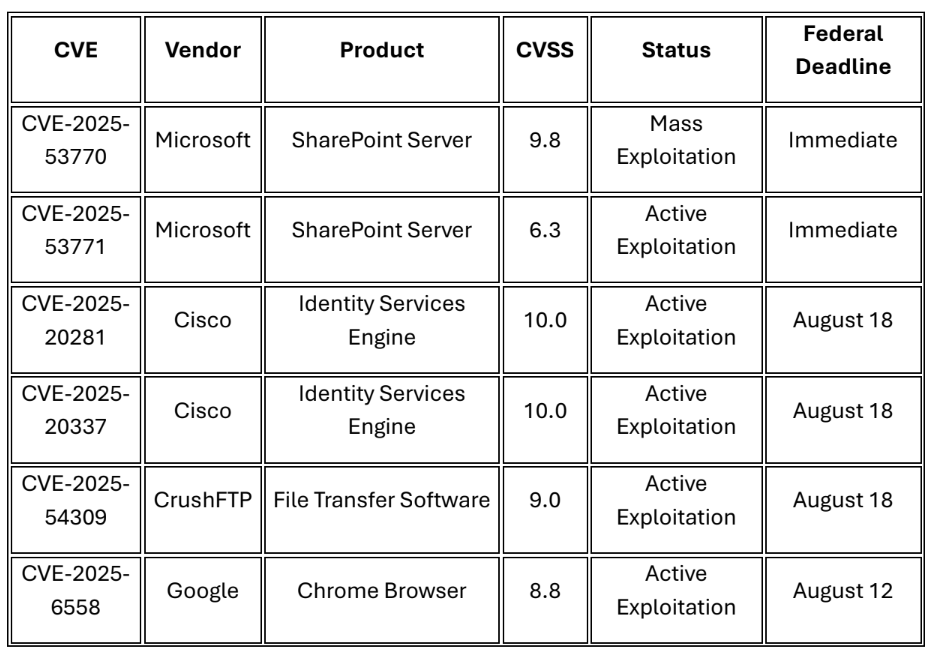
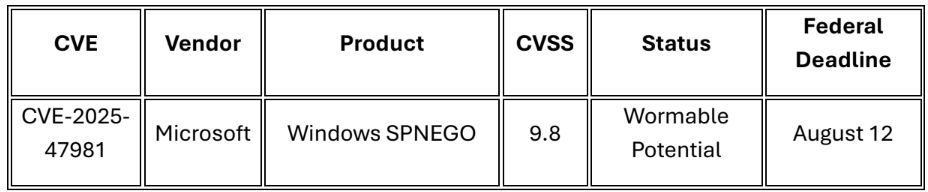
Continuing Active Exploitation
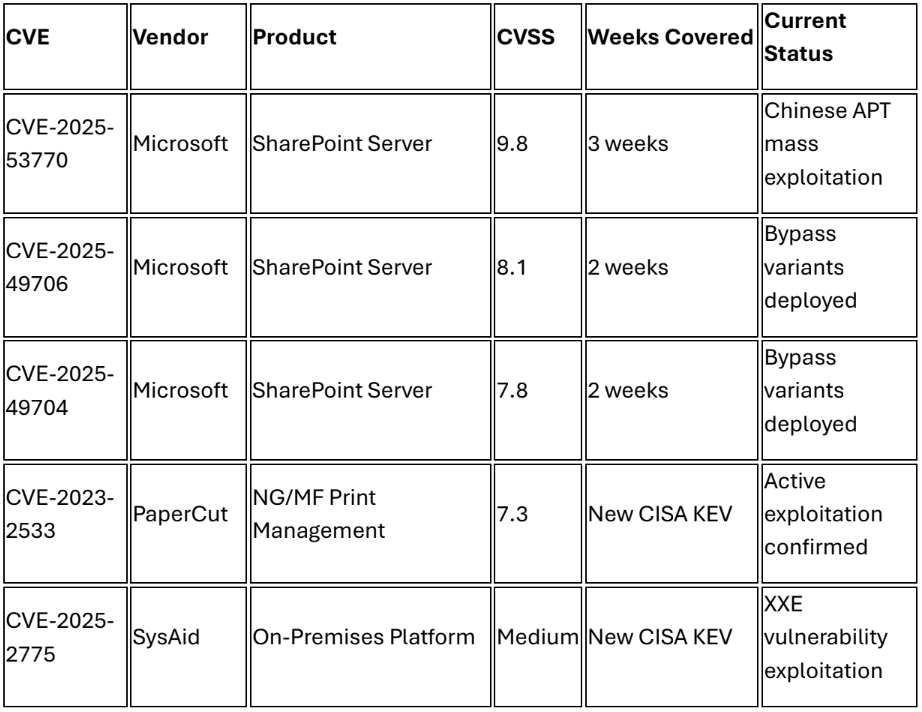
RECOMMENDATIONS
Immediate Actions (0-24 Hours)
• Disconnect all internet-facing SharePoint servers immediately and apply emergency patches for CVE-2025-53770 and CVE-2025-53771 before reconnection
• Assume compromise for any SharePoint servers exposed to internet during July 7 - August 1 exploitation window; rotate all cryptographic material and reset associated credentials
• Monitor SafePay leak sites for Ingram Micro data exposure beginning August 1; prepare downstream supply chain impact assessments for affected vendors
• Apply critical Cisco ISE patches immediately for CVE-2025-20281 and CVE-2025- 20337 to prevent unauthenticated root access to network infrastructure
• Implement enhanced verification procedures for IT help desk access requests to counter Scattered Spider social engineering tactics targeting administrative privileges
- Microsoft Security Blog. (2025, July 22). Disrupting active exploitation of on-premises SharePoint vulnerabilities. https://www.microsoft.com/en-us/security/blog/2025/07/22/disrupting-active-exploitation-of-on-premises-sharepoint-vulnerabilities/
- SentinelOne Threat Intelligence. (2025, July 24). SharePoint ToolShell | Zero-day exploited in-the-wild targets enterprise servers. SentinelOne
- Check Point Research. (2025, July 28). 28th July -- Threat intelligence report. https://research.checkpoint.com/2025/28th-july-threat-intelligence-report/
- TechCrunch. (2025, July 29). Telecom giant Orange warns of disruption amid ongoing cyberattack. TechCrunch.
- Infosecurity Magazine. (2025, July 29). French Telco Orange Hit by Cyber-Attack. Infosecurity Magazine.
- BleepingComputer. (2025, July 28). French telecommunications giant Orange discloses cyberattack. BleepingComputer.
- Dark Reading. (2025, July 31). SafePay claims Ingram Micro breach, sets ransom deadline. https://www.darkreading.com/cyberattacks-data-breaches/safepay-ingram-micro-breach-ransom-deadline
- BleepingComputer. (2025, July 6). Ingram Micro outage caused by SafePay ransomware attack. BleepingComputer.
- Silent Crow. (2025, July 28). Operation Aeroflot: Disrupting Russian aviation infrastructure. Pro-Ukrainian Cyber Operations.
- Belarus Cyber Partisans. (2025, July 28). Joint operation results in massive Aeroflot data destruction. Cyber Partisans Telegram.
- Recorded Future News. (2025, July 29). Silent Crow claims year-long infiltration of Aeroflot networks. The Record.
- Google Threat Intelligence Group. (2025, July 28). Scattered Spider hijacks VMware ESXi to deploy ransomware on critical U.S. infrastructure. The Hacker News.
- CISA. (2025, July 29). CISA and partners release updated advisory on Scattered Spider group. https://www.cisa.gov/news-events/alerts/2025/07/29/cisa-and-partners-release-updated-advisory-scattered-spider-group
- The Hacker News. (2025, July 22). Microsoft links ongoing SharePoint exploits to three Chinese hacker groups. The Hacker News.
- Microsoft Threat Intelligence. (2025, July 31). Secret Blizzard deploys malware in ISP-level AitM attacks on Moscow embassies. The Hacker News.
- United Nations Office on Drugs and Crime. (2025, July 20). Southeast Asian cybercrime industry estimated at billions in annual revenue. UNODC.
- Flashpoint Intelligence. (2025, July 31). Navigating 2025's midyear threats: Insights from Flashpoint's Intelligence Index. https://flashpoint.io/blog/flashpoint-2025-global-threat-intelligence-index-midyear/
- U.S. Department of Justice. (2025, July 25). Arizona Woman Sentenced for $17M Information Technology Worker Fraud Scheme that Generated Revenue for North Korea. DOJ Office of Public Affairs.
- CISA & US Coast Guard. (2025, July 31). CISA and USCG identify areas for cyber hygiene improvement after conducting proactive threat hunt at US critical infrastructure organization. https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-212a
- CISA. (2025, July 29). CISA and partners release updated advisory on Scattered Spider group. https://www.cisa.gov/news-events/alerts/2025/07/29/cisa-and-partners-release-updated-advisory-scattered-spider-group
- Flashpoint Intelligence. (2025, July 31). Navigating 2025's midyear threats: Insights from Flashpoint's Intelligence Index. https://flashpoint.io/blog/flashpoint-2025-global-threat-intelligence-index-midyear/
- Flashpoint Intelligence. (2025, July 31). Navigating 2025's midyear threats: Insights from Flashpoint's Intelligence Index. https://flashpoint.io/blog/flashpoint-2025-global-threat-intelligence-index-midyear/
- CISA & US Coast Guard. (2025, July 31). CISA and USCG identify areas for cyber hygiene
- CISA & US Coast Guard. (2025, July 31). CISA and USCG identify areas for cyber hygiene improvement after conducting proactive threat hunt at US critical infrastructure organization. https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-212a
- CISA & US Coast Guard. (2025, July 31). CISA and USCG identify areas for cyber hygiene improvement after conducting proactive threat hunt at US critical infrastructure organization. https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-212a
- U.S. Department of Justice. (2025, July 25). Arizona Woman Sentenced for $17M Information Technology Worker Fraud Scheme that Generated Revenue for North Korea. DOJ Office of Public Affairs.


